Flip-flops (also called thongs, jandals, pluggers, go-aheads, slaps, slides, step-ins, chankla or a variety of other names throughout the world) are a type of open-toed sandal typically worn in casual situations. They consist of a flat sole held loosely on the foot by a Y-shaped strap that passes between the first and second toes and around either side of the foot. They may also be held to the foot with a single strap over the top of the foot rather than a thong. The name is an onomatopoeia for the sound that is made when the sole slaps the ground while walking in flip-flops.
This style of footwear has been worn by the people of many cultures throughout the world, originating as early as the ancient Egyptians. The modern flip-flop descends from the Japanese zōri, which were popularized in the US after WWII by soldiers returning from the Pacific theater. They are common summer footwear for both genders, and some varieties have even found their way into more formal attire, despite criticism.
read more »
Flip-flops
Recursive Self-improvement
Recursive [ri-kur-siv] self-improvement is the speculative ability of a strong artificial intelligence computer program to program its own software continuously. This is sometimes also referred to as ‘Seed AI’ because if an AI were created with engineering capabilities that matched those of its human creators, it would have the potential to autonomously improve the design of its constituent software and hardware. Having undergone these improvements, it would then be better able to find ways of optimizing its structure and improving its abilities further. It is speculated that over many iterations, such an AI would far surpass human cognitive abilities.
This notion of an ‘intelligence explosion’ was first described by British cryptographer I.J. Good in 1965, who speculated on the effects of superhuman machines: ‘Let an ultraintelligent machine be defined as a machine that can far surpass all the intellectual activities of any man however clever. Since the design of machines is one of these intellectual activities, an ultraintelligent machine could design even better machines; there would then unquestionably be an ‘intelligence explosion,’ and the intelligence of man would be left far behind. Thus the first ultraintelligent machine is the last invention that man need ever make.’
read more »
Stingray Phone Tracker
The StingRay is an IMSI-catcher (International Mobile Subscriber Identity), a controversial cellular phone surveillance device, manufactured by the Harris Corporation. Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across the US. Stingray has also become a generic name to describe these kinds of devices.
The StingRay has with both passive (digital analyzer) and active (cell site simulator) capabilities. When operating in active mode, the device mimics a wireless carrier cell tower in order to force all nearby mobile phones and other cellular data devices to connect to it. The devices can be mounted on cars, airplanes, helicopters, and unmanned aerial vehicles, as well as carried by hand. They are primarily used for surveillance, but can also conduct denial of service attacks (radio jamming).
read more »
Project Blue Book
Project Blue Book was one of a series of systematic studies of unidentified flying objects (UFOs) conducted by the United States Air Force. It started in 1952, and it was the third study of its kind (the first two were projects ‘Sign’ in 1947 and ‘Grudge’ in 1949). A termination order was given for the study in 1969. Project Blue Book had two goals: To determine if UFOs were a threat to national security, and To scientifically analyze UFO-related data. Thousands of UFO reports were collected, analyzed and filed.
As the result of the ‘Condon Report’ (1968), which concluded there was nothing anomalous about UFOs, Project Blue Book was ordered shut down in 1970. Ultimately, Project Blue Book stated that UFOs sightings were generated as a result of: hysteria, fraud, hoaxes, and misidentification. The Air Force continues to provide the following summary of its investigations: ‘There was no evidence indicating that sightings categorized as ‘unidentified’ were extraterrestrial vehicles.’
read more »
Turnspit Dog
In medieval and early modern kitchens, the spit was the preferred way of cooking meat in a large household. A servant known as the ‘spit boy’ or ‘spit jack’ sat near the spit turning the metal rod slowly to cook the food evenly. Mechanical turnspits (‘roasting jacks’) were later invented and were first powered by dogs on treadmills (and then by steam power and mechanical clockwork mechanisms, and presently by electric motors). The Turnspit Dog was a short-legged, long-bodied dog bred to run on a wheel, called a ‘turnspit’ or ‘dog wheel.’
It is mentioned in ‘Of English Dogs’ in 1576 under the name ‘Turnespete.’ English naturalist William Bingley’s ‘Memoirs of British Quadrupeds’ (1809) also talks of a dog employed to help chefs, known as the ‘Kitchen Dog,’ the ‘Cooking Dog,’ the ‘Underdog,’ and the ‘Vernepator.’ In Swedish zoologist Carl Linnaeus’ 18th century classification of dogs it is listed as ‘Canis vertigus’ (‘spinning dog’). The breed was lost since it was considered to be such a lowly and common dog that no record was effectively kept of it. Some sources consider the Turnspit a kind of Glen of Imaal Terrier, others make it a relative of the Welsh Corgi.
read more »
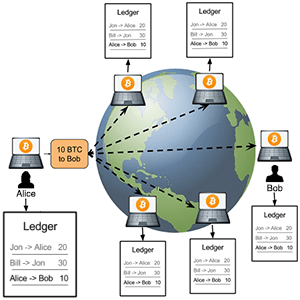
Block Chain
Bitcoin is a cryptocurrency, an online payment system secured by cryptography, released by the pseudonymous Satoshi Nakamoto in 2009. The system is peer-to-peer; users can transact directly without needing an intermediary. Transactions are verified by network nodes containing a public ledger called the block chain. Bitcoin nodes use the block chain to distinguish legitimate Bitcoin transactions from attempts to re-spend coins that have already been spent elsewhere. Bitcoin ‘mining’ is a record-keeping service. Miners keep the block chain consistent, complete, and unalterable by repeatedly verifying and collecting newly broadcast transactions into a new group of transactions called a ‘block.’
A new block contains information that ‘chains’ it to the previous block thus giving the block chain its name. It is a cryptographic hash (scrambled code that represents the block). Miners compute the hash functions to verify them for the network, a task that is intentionally designed to be resource-intensive and computationally difficult so that the number of blocks found each day remains steady. Mining is also the mechanism used to introduce new coins into the system: Miners are paid transaction fees as well as a ‘subsidy’ of newly created coins. This both serves the purpose of disseminating new coins in a decentralized manner as well as motivating people to provide security for the system.
Mosquito Alarm
‘The Mosquito’ or Mosquito alarm is an electronic device used to deter loitering by young people by emitting sound at high frequency that older people have lost the ability to hear. It has two frequency settings, one of approximately 17.4 kHz that can generally be heard only by young people, and another at 8 kHz that can be heard by most people. The maximum potential output sound pressure level is stated by the manufacturer to be 108 decibels. The range of the sound is 140 feet with the sound baffle, and 200 feet without.
The sound can typically only be heard by people below 25 years of age, as the ability to hear high frequencies deteriorates with age (a phenomenon known as presbycusis). Crafty teenagers turned the sounds into a mobile phone ringtone, which could not be heard by older teachers if the phone rang during a class. Mobile phone speakers are capable of producing frequencies above 20 kHz. This ringtone became informally known as ‘Teen Buzz’ or ‘the Mosquito ringtone’ and has since been sold commercially.
read more »
Active Traffic Management
Active traffic management (ATM, also known as, ‘smart lanes’ or ‘managed motorway’) is method of increasing peak capacity and smoothing traffic flows on busy major highways. Techniques include variable speed limits, hard-shoulder running (use of the shoulder as a travel lane during congested periods) and ramp-metering (traffic lights at entrance ramps regulating the flow of incoming traffic). Drivers are alerted to changing conditions by overhead, electronic signs.
It is currently in operation in Birmingham, England. The scheme had initially been criticized by some due to possible safety and environmental concerns, however a Highways Agency report into the first six months of the scheme showed a reduction in the number of accidents and the system was expanded to other highways in the UK. It is seen as a less expensive alternative to widening a road.
read more »
Notel
A Notel, also called Notetel, is a type of portable media player made in China which is popular in North Korea. The device has USB and SD ports, can play DVDs and EVDs (Enhanced Versatile Discs, which are physically identical to DVDs but use a different file format), and contains a radio and TV tuner. The name is a portmanteau of ‘notebook’ and ‘television.’ In China, Notels are no longer popular as of 2015, but sell well in the provinces that border on North Korea, where scarce internet and frequent power outages, as well as their ease of concealment make them very useful.
Notetels have been popular in North Korea since around 2005, significantly facilitating the extension of the ‘Korean Wave’ (‘Hallyu,’ the increase of the popularity of South Korean pop culture) into the communist country. After an earlier crackdown that caused black market prices to drop, the devices were legalized in December 2014 (however, they require a license and the government monitors their use). As of 2015 they are available in some government stores as well as on the black market (Jangmadang ) for around 300 Chinese Yuan (ca. US$ 50), and are present in about half of all households.
The Truman Show Delusion
The Truman Show delusion, informally known as Truman Syndrome, is a type of persecutory/grandiose delusion in which patients believe their lives are staged plays or reality television shows. The term was coined in 2008 by brothers Joel and Ian Gold, a psychiatrist and a neurophilosopher, respectively, after the 1998 film ‘The Truman Show,’ about a man who discovers he is living in a constructed reality televised globally around the clock. Since he was in the womb, all the people in Burbank’s life have been paid actors.
The concept predates this particular film. It was based on a 1989 episode of the ‘Twilight Zone,’ ‘Special Service,’ which begins with the protagonist discovering a camera in his bathroom mirror. This man soon learns that his life is being broadcast 24/7 on TV. Author Philip K. Dick has also written short stories and, most notably, a novel, ‘Time Out of Joint’ (1959), in which the protagonist lives in a created world in which his ‘family’ and ‘friends’ are paid to maintain the delusions.
read more »
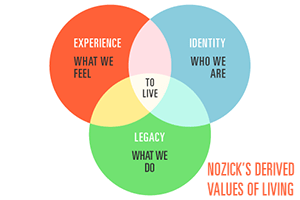
Experience Machine
The Experience Machine or Pleasure Machine is a thought experiment put forward by philosopher Robert Nozick in his 1974 book ‘Anarchy, State, and Utopia.’ He describes a choice between everyday reality and an apparently preferable simulated reality as a refutation of ethical hedonism, the idea that people have the right to do everything in their power (that doesn’t infringe on others) to achieve the greatest amount of pleasure possible to them.
If the primary thesis of hedonism is that ‘pleasure is the good,’ then any component of life that is not pleasurable does nothing directly to increase one’s well-being. This is a view held by many value theorists (who study how, why, and to what degree people value things), but most famously by some classical utilitarians (who believe that the morally best action is the one that makes the most overall happiness or ‘utility’ (usefulness). Nozick argues that if he can show that there is something other than pleasure that has value and thereby increases our well-being, then hedonism is defeated.
read more »
Pascal’s Mugging
In philosophy, Pascal’s mugging is a thought experiment demonstrating a problem in expected utility maximization. A rational agent should choose actions whose outcomes, when weighed by their probability, have higher utility. But some very unlikely outcomes may have very great utilities, and these utilities can grow faster than the probability diminishes. Hence the agent should focus more on vastly improbable cases with implausibly high rewards. The name refers to Pascal’s Wager (an argument by French mathematician Blaise Pascal that the potential cost of not believing in God is higher than the cost of believing), but unlike the wager does not require infinite rewards. This removes any objections to the dilemma that are based on the nature of infinity.
British philosopher Jeremy Bentham’s: ‘The greatest good for the greatest number’ formed the foundation of utilitarianism, which says that the morally best action is the one that makes the most overall happiness or ‘utility’ (usefulness). Pascal’s mugging points out that in extreme case this philosophy can fail. The term for this problem was coined by artificial intelligence researcher Eliezer Yudkowsky in the ‘Less Wrong’ internet forum and his original example was: ‘Now suppose someone comes to me and says, ‘Give me five dollars, or I’ll use my magic powers from outside the Matrix to run a Turing machine that simulates and kills [trillions of] people.’ Even though the chance of this actually happening is negligible, the threatened outcome is so large a rational agent must accede to the demand.
read more »